CVE Wednesday - CVE-2024-20439
Introduction
Cisco recently released an advisory for CVE-2024-20439 here. (nvd) Please note I did not discover this vulnerability, I just reverse engineered the vulnerability from the advisory
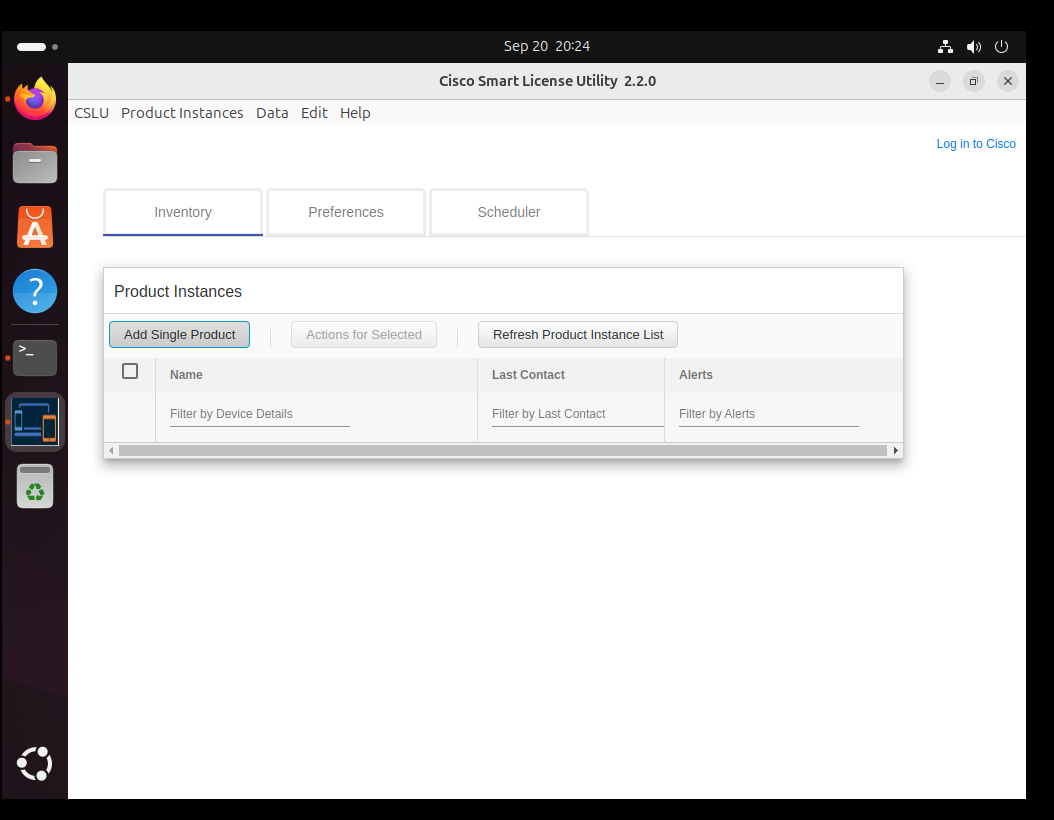
This vulnerability is a hardcoded static password that can be used to access licensing data in Cisco Smart Licensing Utility. Cisco Smart Licensing Utility can be downloaded from Cisco here
I downloaded all versions and did some snooping around looking for the hard coded password. I wanted to figure out what the hard coded password is as well as to assess the impact of the vulnerability.
tl;dr: The password is Library4C$LU.
Target Application
The target software application can be downloaded for Windows or Linux. I downloaded the .deb installer file for Linux and extracted the contents using the ar vx $FILENAME command.
The Cisco Smart Licensing Utility is an electron application built on top of a REST API that is written in golang. The REST API runs in a different process, but it runs on the same host as the Electron application. The electron application makes HTTP requests to localhost for its state changing data operations. The REST API listens on all network interfaces by default.
I used a Ghidra Golang Extension (available here) to make sense of the cslu-api binary.
Electron Component
Inside the installer .deb file is resources/app.asar. An .asar file is an electron archive, and it can be extracted using the command npx @electron/asar extract $ASAR_FILE_PATH ..
Inside the .asar file is ServicePools/APIClient.js:
Version 2.2.0:
"use strict";
Object.defineProperty(exports, "__esModule", { value: true });
var axios_1 = require("axios");
var https = require("https");
var rxjs_1 = require("rxjs");
var APIClient = /** @class */ (function () {
function APIClient(config) {
this.protocol = "http";
this.apiHost = "localhost";
this.apiPort = 4596;
this.apiEndpointPath = "/cslu/v1";
this.basicAuthUserName = "cslu-windows-client";
this.basicAuthPassword = "Library4C$LU";
if (!!APIClient.getInstance()) {
return APIClient.getInstance();
}
[...]
Version 2.3.0:
"use strict";
Object.defineProperty(exports, "__esModule", { value: true });
var axios_1 = require("axios");
var https = require("https");
var rxjs_1 = require("rxjs");
var APIClient = /** @class */ (function () {
function APIClient(config) {
this.protocol = "http";
this.apiHost = "localhost";
this.apiPort = 8180;
this.apiEndpointPath = "/cslu/v1";
this.basicAuthUserName = "cslu-windows-client";
this.basicAuthPassword = "";
if (!!APIClient.getInstance()) {
return APIClient.getInstance();
}
else {
this.createNewAxiosInstance(config);
}
[...]
We can see the credentials are cslu-windows-client:Library4C$LU and that the REST API uses HTTP Basic Authentication.
API Application
The API application binary lives in resources/API-BINARIES/cslu-api. This is the Golang binary.
Version 2.2.0:
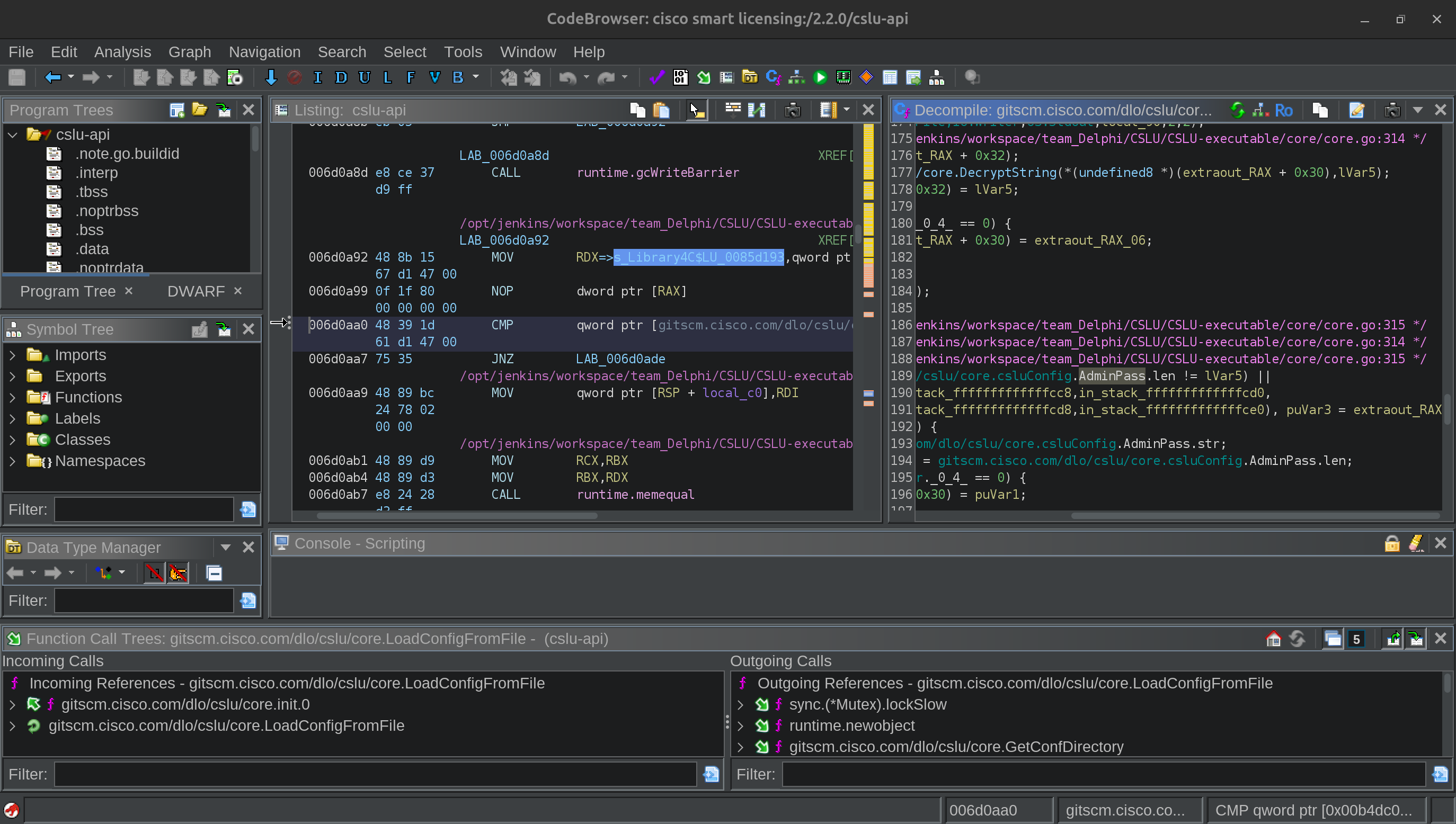
Version 2.3.0 of this function is simplified from 2.2.0 shown above and does not include the password string. Likewise, grepping through the extracted contents of both the .deb and .asar files for version 2.3.0 indicates that particular string is not present in this new version.
The Ghidra Extension simplifies the decompilation output for the admin password to gitscm.cisco.com/dlo/cslu/core.csluConfig.AdminPass. It is easier to see the admin password string value in the disassembly output instead.
Analysis
This is a particularly nasty vulnerability because the cslu-api process listens on all network interfaces. That means an attacker who can access the host machine over the network can make authenticated web requests to the API using this well known password on vulnerable versions.
Versions 2.0.0 and 2.1.0 use the same credentials as 2.2.0.
Next Steps
I didn’t go much further in analyzing the REST API and the underlying data store that is accessible through the REST API. It looks like the application stores inventory and associated license data. Next steps could be writing a tool (or metasploit module) that uses the credentials to dump data from a vulnerable instance.